
Ansible is an open source configuration management tool for configuring IT systems. One of the primary benefits of Ansible is the agentless architecture that utilizes the SSH and WinRM protocols to interact with remote Linux and Windows systems respectively. These protocols are native to the operating systems and typically require minimal configuration to utilize. The agentless architecture coupled with the native protocols enables Ansible to be deployed without the need for additional management infrastructure. While on the one hand this is a benefit, it is also poses a challenge for organizations that have security policies in place that prohibit the use of SSH or WinRM access to systems. Morpheus helps overcome this challenge with its command bus for secure Ansible execution.
Other configuration management tools overcome this security challenge through the use of an agent. The agent initiates the communication with the management server and eliminates the need for inbound access to the remote system from the management server. Morpheus utilizes the same mechanism with the Morpheus agent. A concern that many administrators may have is if the agent is resource intensive and the ease of deployment. The agent is lightweight and in most scenarios the agent is automatically installed by the Morpheus platform.
The Morpheus agent provides a number of benefits in addition to the command bus for playbook execution.
Find additional information about the Morpheus agent in the Morpheus agent documentation.
The diagram below provides an overview of how the Ansible playbook execution is different with and without Morpheus command bus execution.
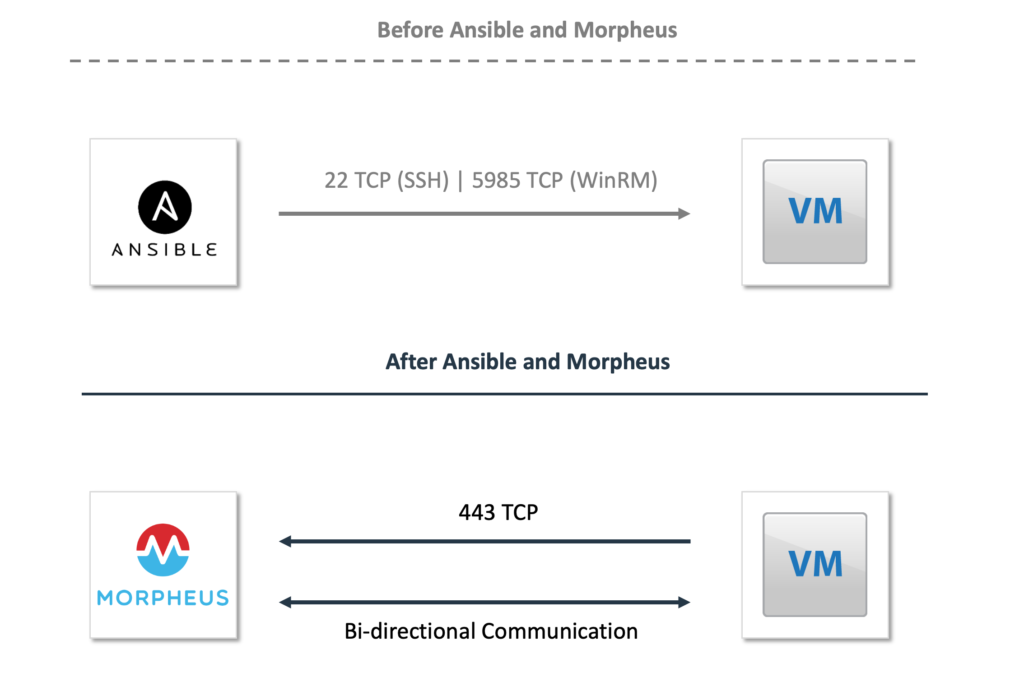
Secure Ansible Execution Diagram
Without Morpheus Command Bus
Without the Morpheus command bus Ansible executes the playbook and communicates with the remote system via SSH or WinRM. Inbound access for SSH and WinRM must be allowed on the remote systems. On Windows systems the secure configuration of WinRM is often a challenge and the Morpheus agent simplifies the process of executing Ansible playbooks on those systems.
With Morpheus Command Bus
The Morpheus agent initiates the creation of a bidirectional communication channel with the Morpheus platform. The agent initiates the connection over port 443 to the Morpheus appliance with TLS encryption. Once the channel has been established it is used by Ansible during playbook execution. This eliminates the need to use SSH or WinRM as the communication protocols for managing systems.
The Morpheus command bus extends the benefits of Ansible to environments that restrict SSH and WinRM access. This enables organizations that are using or looking to use Ansible to align with IT security policies. Find additional information about the Morpheus and Ansible integration in the Using Morpheus to make Ansible better whitepaper.
Try Morpheus Community Edition
The Morpheus Community Edition lets you fully experience the Morpheus platform including nearly all features and capabilities! Register at Morpheus Hub and try it in your home lab or test environment today!