Shadow IT is the use of technology without the approval and governance from IT Operations or Security teams. It most often happens when employees find it faster to bypass IT and Security approvals.
The answer? Morpheus enables self-service provisioning with built in guardrails so employees get what they want in real-time while still maintaining security posture to eliminate shadow IT.
Roles determine Feature, Cloud, and Catalog access. Entire UI and API sections can be disabled based on access levels.
Morpheus supports authentication and role mapping via identity management integration to Active Directory, Azure AD, SAML, OKTA, etc. including SSO and MFA.
Define access by adding clouds to groups which could represent projects, development phases, or organizational units.
Group permissions apply to resources like networks, data stores, resource pools, and folders. Lifecycle, usage, and compliance policies get assigned to complete the RBAC picture.
Tenants can have their own identity providers, white label settings, user roles, and clouds defined.
Morpheus can even add multi-tenant sharing to typically single-tenant platforms like VMware ESX and Nutanix AHV.
For example, add a VMware cluster to the master tenant then split access securely across isolated tenants including storage and network access.
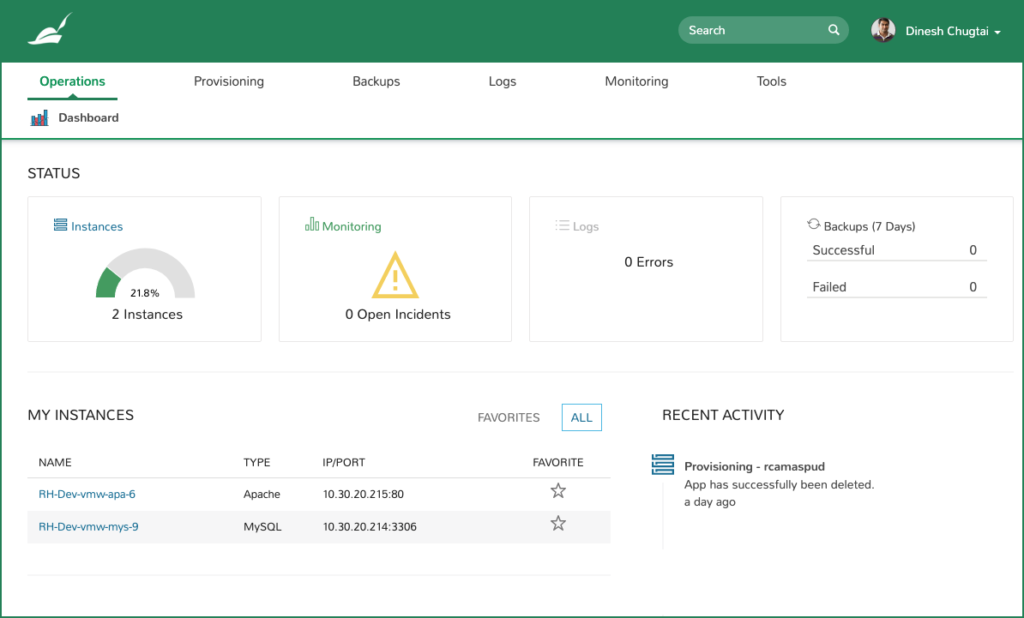
Make sure teams are always using the right golden templates, embed security agents into provisioning catalog items, and set policy to restrict cloud access.
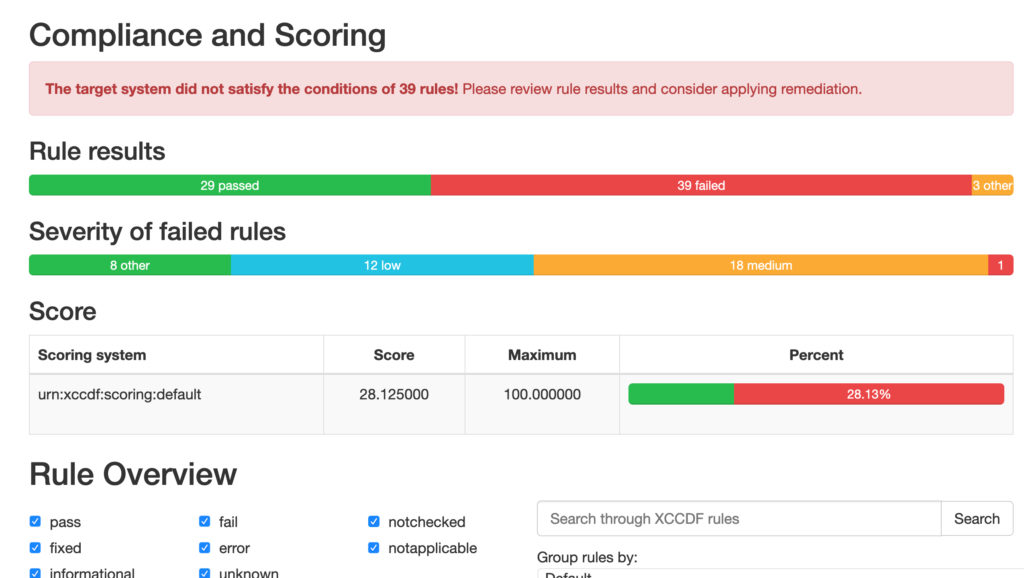
Leverage Security Scan Jobs to create and schedule SCAP program (Security Content Automation Program) scans for groups of managed systems.
Import SCAP files, schedule scan jobs, and view the results including risk scores and severity to help prioritize remediation efforts.
Scope policies to Users, Roles, Groups, Clouds, Tenants and Global to give Admins full control of their hybrid and multi-cloud environments.

Naming, Provisioning Approval, Expiration, Shutdown, Removal, Power Schedules, etc.

Max containers, cores, memory, storage, VMs as well as budgets and resource quotas.

Tag enforcement, User Creation, User Groups, Backups, Delayed Removal, Message Alerts, etc.

Force execution of workflows to apply custom policies for security, compliance, and more.