
Recent data breaches and ransomware attacks have prompted organizations of all sizes to scrutinize their IT security posture. Continuously securing hundreds or thousands of systems is a daunting task. The Center for Information Security has developed benchmarks or recommended security controls for hardening IT systems. The benchmarks include dozens of technical controls that need to be applied to systems. Application and continuous enforcement of the controls at scale is a challenge many organizations face. Morpheus and Puppet Enterprise help solve this problem by simplifying the process of applying and enforcing CIS controls on an organization’s workloads in an automated fashion.
In this blog post we’ll walk through how to deploy a CIS hardened linux virtual machine. Puppet recently published a blog post on enforcing CIS benchmarks on a linux system using Puppet. We’ll use this as the foundation for enforcing CIS controls on the linux virtual machine we deploy with Morpheus. The goal of the solution is to easily deploy a PostgreSQL database on a CIS hardened operating system using Morpheus and Puppet Enterprise.
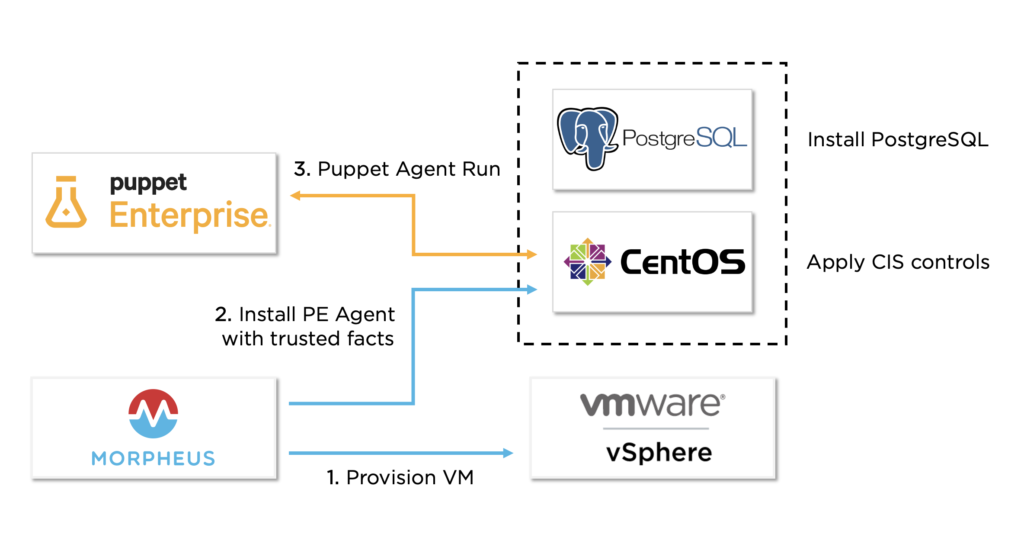
The following steps will be used to automate the end to end provisioning:
Before we jump right into building out the solution we need to understand how we’ll integrate Morpheus and Puppet Enterprise by understanding Puppet roles and profiles. Roles and profiles are a concept for organizing puppet code in a manner that simplifies the application of puppet code. Profiles are high level building blocks that are combined to define a role. Roles are then associated with a virtual machine or server. We’ll take a look at the role and profile structure for our scenario.
Linux Baseline Profile
We’ll create a base or baseline profile for our linux systems in Puppet. The baseline profile defines the software and system configuration for all of our Linux systems. In our example this is where we’ll include the Puppet module for enforcing CIS controls.
Database Role
Roles define the business function of the virtual machine. The common pattern for assigning a Puppet role with a server or virtual machine is to populate the pp_role trusted fact of a node. Puppet trusted facts are facts that are extracted from a node’s certificate. These are embedded into the node’s SSL certificate during the CSR creation process. In our example we want to set the pp_role for our node to database.
Node Classification
We need a way to tell Puppet Enterprise what code a node should run during a Puppet agent run. In order to use the role definition we just talked about in a dynamic fashion we’ll add the following code to the manifest/site.pp Puppet file in our control repo. If the node has a pp_role trusted fact defined then include the role::${role} class which would map to role::database in our example.
node default {
if $trusted['extensions']['pp_role'] {
$role = $trusted['extensions']['pp_role']
include "role::${role}"
}
}The next step in the process is automating the installation of the Puppet Enterprise agent. Puppet Enterprise includes a simple agent installation script that we’ll use to install the Puppet Enterprise agent on the provisioned virtual machine.
Morpheus Task
We’ll create a Morpheus task that installs the Puppet Enterprise agent and triggers a Puppet agent run. During the agent bootstrap process the node’s SSL certificate needs to be signed by the Puppet server in order to use Puppet for system configuration. Out of the box this is a manual process which poses a problem for automated virtual machine provisioning. We’ll use policy based autosigning to automate the process. The code below runs the PE agent install script with a specified challenge password, pp_role, and pp_environment. Secure retrieval of the challenge password occurs via a Cypher call in the script. The pp_role environment variable associated with the instance defines the pp_role trusted fact. The instanceContext or instance’s environment defines the pp_environment trusted fact.
#!/bin/bash
curl --insecure "https://morpheuspe01.morpheus.local:8140/packages/current/install.bash" | sudo bash -s -- custom_attributes_challengePassword=<%=cypher.read('secret/pechallenge')%> extension_requests_pp_role="<%= evars.pp_role %>" extension_requests_pp_environment="<%=instance.instanceContext%>" --puppet-service-ensure stopped
/usr/local/bin/puppet agent -t
/usr/local/bin/puppet agent -t
/usr/local/bin/puppet agent -t
exitcode=$?
if [ $exitcode -eq 0 -o $exitcode -eq 2 ]; then
exit 0
else
exit $exitcode
fiMorpheus Provisioning Workflow
We need to add the task to a provisioning workflow in order to tie it to an instance. The provisioning workflow in this example includes the Puppet Enterprise agent installation tasks and a node purge task used during decommissioning. We won’t dig into the decommissioning task in this blog but the task calls Puppet Enterprise to purge the node and free up the node license once it has been destroyed.
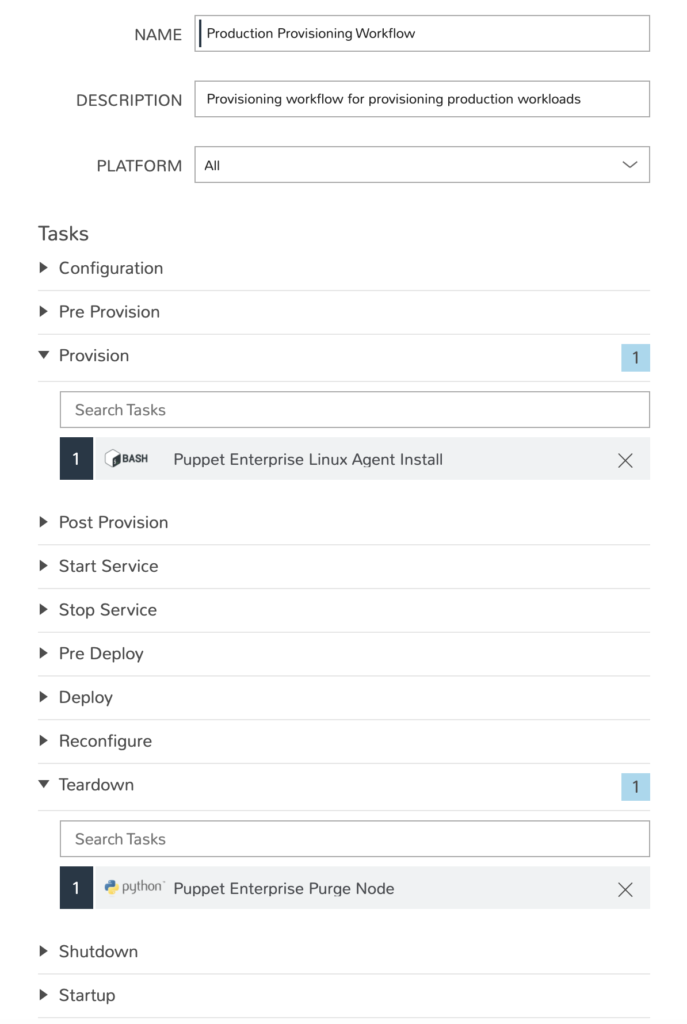
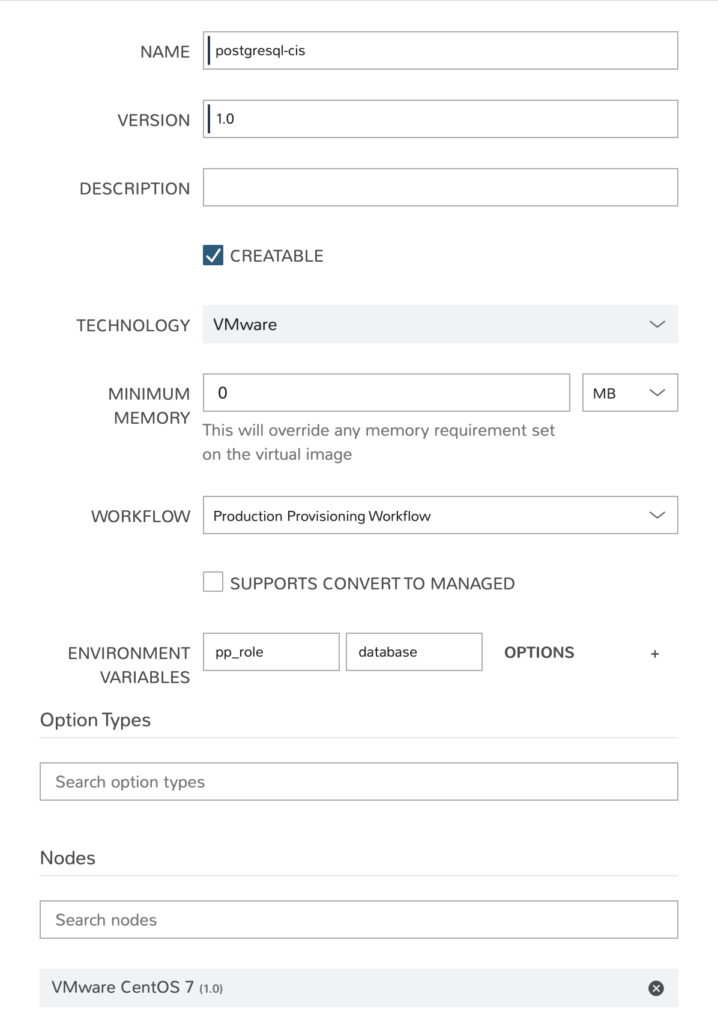
Now that we have the building blocks of the automation we now need to tie it all together in a Morpheus custom instance. The Morpheus node type used is a vanilla CentOS image since we’ll be configuring the system using Puppet Enterprise. The provisioning workflow and pp_role environment are specified at the instance layout layer. An example instance layout is show below. Finally, the instance type simply references the instance layout.
At this point we can provision an instance that incorporates the hardening automation but we can simplify the request process by creating a service catalog item. In this example we’ve created a catalog item that includes two custom options. One to specify the version of PostgreSQL and the other to specify the size of the virtual machine.
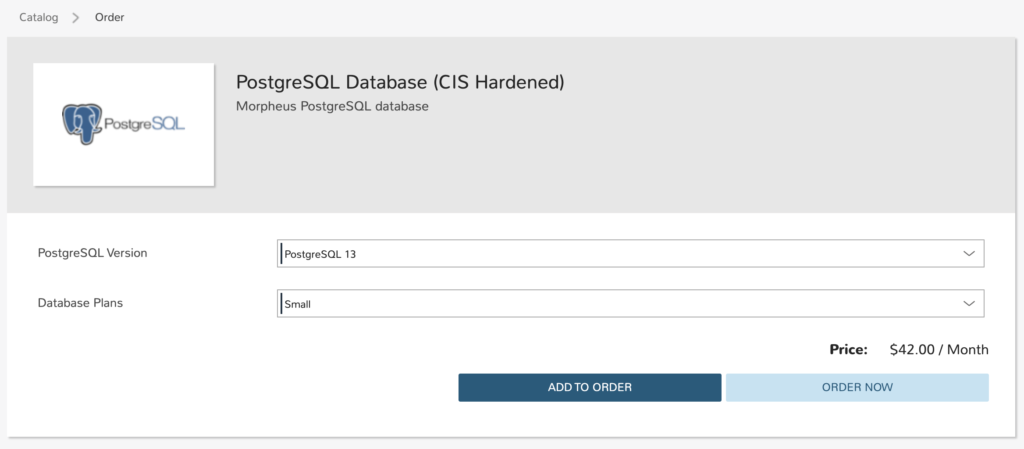
The instance is ordered by clicking the Order Now button and waiting until the provisioning has completed.
With the catalog item ordered we can validate that the automation worked successfully by going into the Puppet Enterprise console. The node reports show the status of the puppet runs and whether there were any corrective changes.
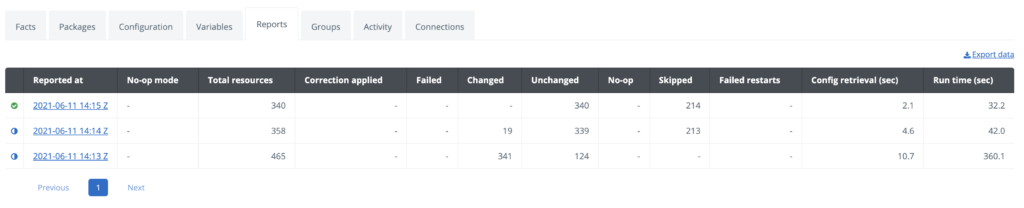
The report includes detailed information about the changes applied by the PostgreSQL and CIS modules.
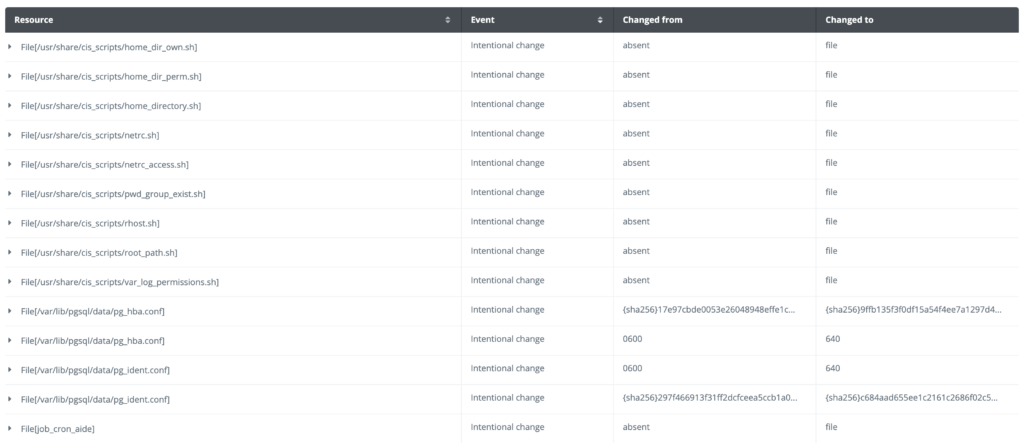
In this blog post we looked at how to deploy a CIS hardened virtual machine in an automated fashion using Morpheus and Puppet Enterprise. This enables IT organizations to deliver on the speed and security that the business needs to move quickly. Hardening of the PostgreSQL database is also possible with Puppet Enterprise.
Try Morpheus Community Edition or Get a Demo
The Morpheus Community Edition lets you fully experience the Morpheus platform including nearly all features and capabilities! Register at Morpheus Hub and try it in your home lab or test environment today! Interested in learning more about Morpheus from one of our cloud transformation experts? Schedule a demo to walk through how Morpheus can help your organization here.