New approaches are required to secure data in an age of networks without boundaries. Although traditional approaches to internal IT security have been rendered obsolete, many tried-and-true techniques are adaptable to the cloud era. Here are five aspects to consider when crafting your company’s data security plan.
If you remain unconvinced of the need to update your internal data security approach to make it cloud-ready, consider the fate of Smyth Jewelers, a retail jewelry chain headquartered in Maryland. Robert Uriarte and Christina Von der Ahe of the Orrick Trade Secrets Group write in a June 16, 2017, article on JD Supra that the company found itself locked out of its Dropbox account after the departure of the lone employee responsible for maintaining the account.
Among the proprietary company documents stored in the account were business plans, vendor details, confidential information about employees, customer lists, purchase histories, and “valuable customer account metrics,” according to the authors. All it took to place these vital data resources off limits was for the employee to change the email address associated with the Dropbox account from the person’s company email address to his private address.
As they say, hindsight is 20-20. The quandary Smyth Jewelers found itself in was easily preventable. To ensure your organization’s cloud data is protected against attacks from the inside, follow these simple steps. As they also say, an ounce of prevention is worth a pound of cure.
Tip #1: Safeguard your cloud account details
The obvious approach to prevent a disgruntled employee from locking down the company’s cloud assets is to establish administrative login credentials that IT controls. Another layer of prevention is available by enabling the cloud service’s notifications whenever an important system setting changes. To be effective, alerts must reach the right parties in a timely manner.
Further, use a cloud service that provides multiple tiers of access services allows you to designate critical documents and resources that receive an added layer of protection. These may be as simple as a folder-level password, or file-level restrictions on viewing, printing, downloading, or editing a document.
Tip #2: Think in terms of ‘governance’ rather than ‘controls’ and ‘monitoring’
There are few rules enforced by IT departments that employees can’t figure out how to break. A better approach for managing information risk in your company is governance, according to Matt Kelly of RadicalCompliance in a June 19, 2017, article on Legaltech News. By focusing on governance, you devise policies for handling data that apply to everyone in the organization. The policies serve as a framework that employees can use for making judgments about information as new, unanticipated risks arise.
Kelly explains the key difference between governance and controls: governance educates users about the reasons why they need to be mindful of the risks associated with the information they handle; while controls are perceived as a fixed set of rules that apply in specific situations.

Organizations encountered an average of 23.2 separate cloud-related threats per month in the fourth quarter of 2016, an 18.4 percent increase from the year-earlier period; the highest single category was insider threats, reported by 93.5 percent of companies. Source: Skyhigh Networks
Typical scenarios of information risk are employees who expose sensitive company data on an insecure cloud app, who collect private information from minors without acquiring their parents’ consent, and who destroy data that needs to be preserved for litigation. No set of controls would prevent these occurrences, but in each case, employees mindful of the risks inherent in these situations via governance would know how to respond accordingly.
Tip #3: Implement multifactor authentication, without ticking off users
The single most effective way to prevent unauthorized access to your company’s cloud assets is by using two-factor or multifactor authentication. The single most likely way to turn users against you is by implementing multifactor authentication in a way that makes it harder for employees to get their work done. You have to find the middle ground that delivers ample protection but isn’t too onerous to workers.
In a June 21, 2017, article on TechTarget, Ramin Edmond describes the single sign-on (SSO) technique as a way to strengthen authentication without overburdening employees. SSO creates two layers of authentication, but users only need to be authenticated in both layers once to gain access to a range of apps, databases, and documents. Mobile implementations of SSO allow secure access to multiple mobile apps after a single two-factor authentication.
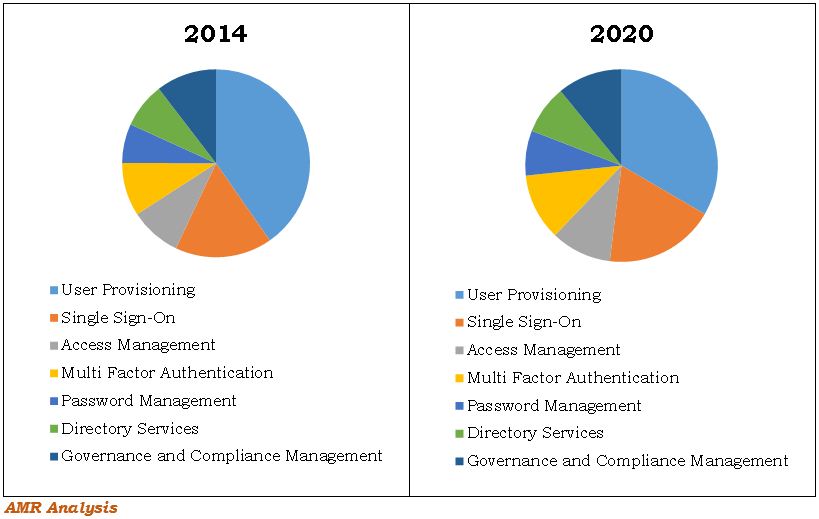 Multifactor authentication and single-sign on will account for larger shares of the global cloud identity access management market in 2020. Source: Allied Market Research
Multifactor authentication and single-sign on will account for larger shares of the global cloud identity access management market in 2020. Source: Allied Market Research
Tip #4: Work with HR to educate and train users about data security policies
Responsibility for crafting data security policies and training employees in the application and enforcement of those policies is shared by the human resources and IT departments. In many companies, IT either takes on too much of the job of employee education at the exclusion of HR or attempts to offload the bulk of the training work to HR.
In a June 21, 2017, article on JD Supra, Jennifer Hodur identifies three areas where HR and IT need to work together:
Tip #5: Be stingy in granting requests for privileged accounts
Haystax Technology recently conducted a crowd-based survey of 300,000 members of the LinkedIn Information Security Community about their approach to insider threats. Security Intelligence’s Rick M. Robinson reports on the survey results in a June 22, 2017, article. Sixty percent of the survey respondents identified privileged users as the source of internal data breaches.
Not all the breaches traced back to a compromised privileged account were malicious in nature. The IT pros surveyed claim negligence and old-fashioned mistakes are the sources of a great number of serious data breaches and data loss. Contractors and temporary workers were identified by 57 percent of the survey respondents as the cause of internal data breaches, whether because they are less loyal or have not been trained in the company’s data security policies.