When it comes to regulatory compliance, some IT departments are in need of an attitude adjustment. Confirming your organization complies with rules governing the protection of sensitive data is no longer an onerous task to be avoided at all costs. Forward-thinking companies now realize their cloud compliance efforts are the cornerstone of realizing the cost, performance, efficiency, and security benefits of cloud services.
There’s no mystery about why companies large, small, and in between are adopting multi-cloud strategies. The three primary reasons cited by Gigaom’s Tim Crawford in an October 19, 2017, article are to prevent being locked into a single cloud provider; to take advantage of the best of breed in specific service and tool categories; and to evaluate several competing cloud services prior to focusing on and building around a single service.
Many companies taking the multi-cloud route are surprised to discover that dealing with multiple cloud services facilitates compliance. For example, few industries take compliance more seriously than financial services. In an October 6, 2017, post on Data Center Knowledge, Sean Finnerty cites a 2015 SANS survey (pdf) that found 71 percent of financial firms choose to keep compliance controls in-house rather than on public cloud services.
In fact, a multi-cloud setup provides the logging, control, classification, redundancy, and maintenance required to guarantee compliance with such regulations as the Payment Card Industry Data Security Standard (PCI DSS), the Gramm-Leach-Bliley Act (GLBA), and Europe’s General Data Protection Regulation (GDPR).
Governance: The key to unlocking all the cloud’s benefits
According to Finnerty, virtual environments streamline regulatory compliance by offering high availability, scalability, and multilayer security that lets you apply protections with pinpoint accuracy. Datamation’s Christine Taylor goes even further, explaining in an April 13, 2017, article that the goal of cloud governance is to manage IT processes “to receive maximum value from cloud computing investments.”
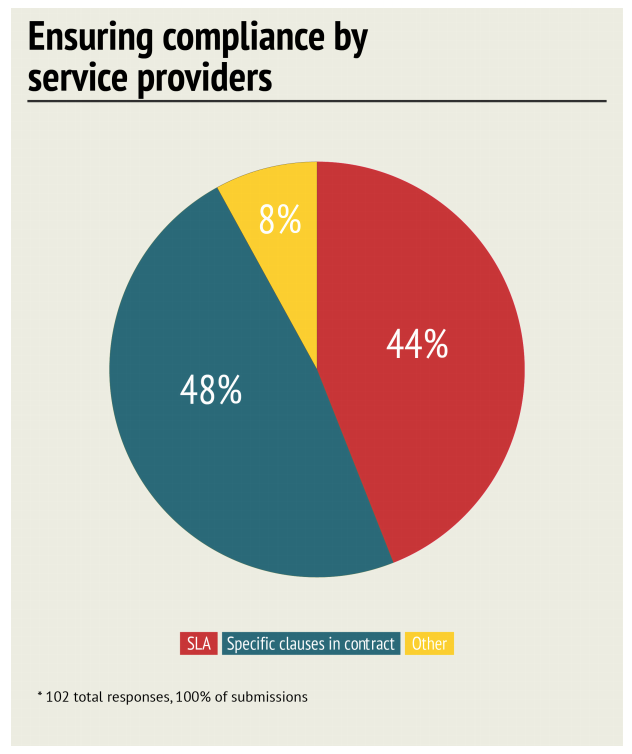
The most popular method used by companies to ensure cloud services meet compliance requirements is contract clauses (48 percent), followed by SLAs (44 percent) and audits (8 percent). Source: SANS Institute
Investing the time and resources required to implement a business-wide cloud governance initiative allows companies to realize “significant cost savings” from their management processes and cloud frameworks, according to Taylor. Four important points to raise with cloud service providers are listed below:
Compliance enhances efficiency of cloud implementations
According to the results of a 2016 survey of enterprise IT pros by research firm Clutch, the regulation receiving the most attention of data managers is the Cloud Security Alliance (CSA), which 39 percent deem necessary for their cloud data. Clutch’s Andrew Miller writes in an article on the Whir that the CSA’s Certificate of Cloud Security Knowledge guarantees that the provider is knowledgeable in the design, construction, and maintenance of cloud environments. The Security, Trust & Assurance Registry (STAR) program of the CSA raises the bar even higher, offering “ toughest set of cloud security regulations in the industry,” according to Miller.
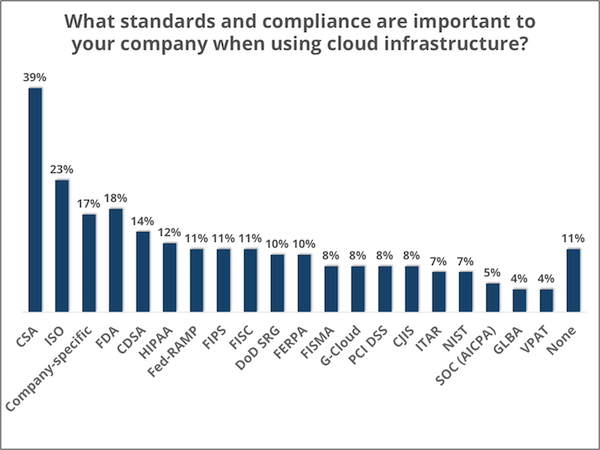
The Cloud Security Alliance is the regulation cited by most enterprise IT departments as a requirement before they will commit their sensitive data to a cloud service. Source: Clutch
The next most popular cloud standard, required by 23 percent of the enterprise IT managers surveyed, is the International Organization of Standards’ ISO/IEC 27018:2014, which governs the storage and processing of personally identifiable information (PII). Cloud services that have earned certification for all of ISO 27001 are considered to be compliant with ISO/IEC 27018:2014.
Compliance with U.S. Food and Drug Administration’s regulations pertaining to electronic records (Chapter 11: Electronic Records; Electronic Signatures) was cited by 23 percent of the IT managers surveyed by Clutch as a requirement for their cloud service providers. In addition, 18 percent of enterprise IT departments insist on compliance with standards of the Content Delivery & Security Association (CDSA). This entails internal risk assessments by cloud services, documentation of security systems and processes, review by a CDSA auditor, a surveillance audit after six months, and an annual audit to maintain certification.
Challenges of confirming HIPAA and FedRAMP compliance by cloud services
While the data-protection requirements built into the Health Insurance Portability and Accountability Act of 1996 (HIPAA) affect only organizations that conduct electronic healthcare transactions, a violation of the HIPAA rules can result in a multi-million-dollar fine. For example, the maximum fine for a single HIPAA violation is $1.5 million. A breach involving thousands of patient records, such as the one reported by New York-Presbyterian Hospital and Columbia University in 2014, may put an organization on the hook for a fine as high as $4.8 million.
Cloud providers may claim to be HIPAA-compliant, but as Clutch’s Miller points out, the U.S. Department of Health and Human Services (HHS), which oversees HIPAA, does not certify providers. Organizations are responsible for ensuring their applications are HIPAA-compliant, using the HHS’s own audit protocols.
Federal government agencies adopting cloud services must ensure their providers comply with the Federal Risk and Authorization Management Program (FedRAMP), a framework that uses third-party assessment organizations (3PAO) to confirm that a cloud service’s data safety measures are transparent and consistent with the agencies’ security policies. Ramona Adams writes in a September 29, 2017, post on ExecutiveGov that the new FedRAMP Tailored baseline is designed to make it faster and easier for agencies to authorize “low-impact software-as-a-service platforms.”
The massive compliance headache on the horizon: GDPR
The calendar may still say “2017,” but many IT managers — and all of those whose companies operate in Europe — are thinking long and hard about May 2018. That’s when the European Union’s General Data Protection Regulation (GDPR) takes effect. Adam Shepherd writes in an October 12, 2017, article on the UK site CloudPro that companies in the U.S. are most likely to be “caught by surprise” by the GDPR’s penalties for non-compliance.
The GDPR sets fines for failing to protect sensitive consumer data as high as 20 million euros or 4 percent of the firm’s “global annual turnover,” whichever amount is higher. Shepherd quotes Box executive David Benjamin as stating that had the Equifax breach occurred when GDPR was in effect, it would have made Equifax subject to a fine of $60 million or greater because the breach affected hundreds of thousands of British citizens.
A report released recently by research firm Netskope on the GDPR readiness of cloud services found that only 24.6 percent of the cloud services currently used by enterprises received a GDPR-readiness rating of “high.” Factors considered in determining the services’ readiness include the location of cloud-stored data, the level of encryption, and the specifics of data processing agreements.
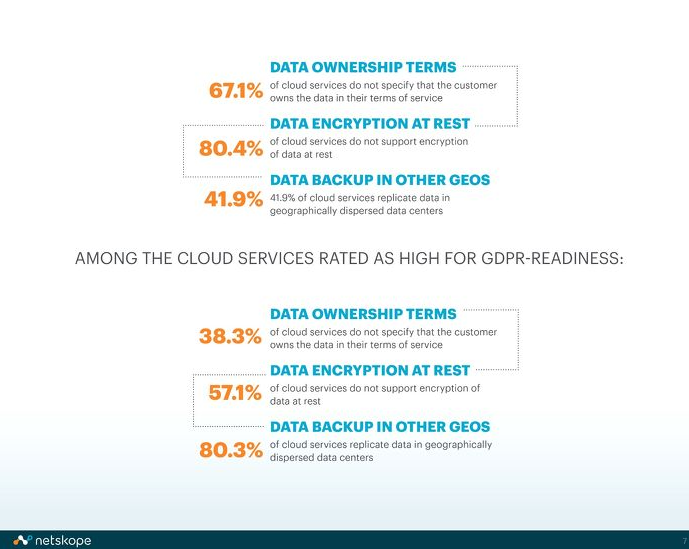
Of the 75 percent of cloud services not yet in compliance with GDPR, 67.1 percent do not specify in their terms of service that customers own the data, 80.4 percent don’t encrypt data at rest, and 41.9 percent replicate data in geographically dispersed data centers. Source: Netskope, via Gigabit
A one-stop resource for companies preparing for GDPR compliance is the Information Security Forum’s GDPR Implementation Guide, which takes a two-phase approach:
It’s time for organizations to move cloud compliance off the back burner. Careful planning of your compliance efforts will result in faster and more-efficient IT operations, while also minimizing the risk of a costly data breach. Think of your compliance efforts as the best form of insurance — the type that can prevent a disaster that has the potential of putting your company out of business.