IP addresses are typically an extremely important part of a network, and managing them can become pretty difficult as the number of IP addresses used on your network increases. With more and more of these being used all the time for applications, databases, microservices, and more, managing all of the necessary IP addresses becomes incredibly important, as the ability for the machines to communicate with one another could make the difference between working services and dreaded downtime.
We currently live in an IP dependent world; the explosion of IP enabled devices such as smartphones, laptops, tablets and other random devices in the workplace has made today’s enterprise networks more dynamic and complex.
Source: Gabriel Lando
IP Address Management (IPAM) is a way in which you can track and manage the IP address space on your network. Typically, IPAM integrates DHCP and DNS, which allows for changes in one to be seen by the other. This allows updating to occur automatically when a change is detected in one or the other.
When it comes to network and machine security, access to IPAM data can make it far easier to detect potential breaches or abuse within your infrastructure. IPAM data include information such as the IP addresses in use, what devices each IP is assigned to, the time each was assigned and to whom each IP was assigned.
This information can be helpful in identifying patterns that indicate security breaches or other abuses of your network. Of course, preventing or bringing to an end such security issues is of extreme importance in order to maintain data integrity and the health of your network and systems.
IPAM can also be helpful when it comes to compliance. Certain internal policies can be enforced using IPAM data and a network access control (NAC) system. For example, before access is granted to your network, the NAC, with help from IPAM information, can determine if your antivirus software is up to date, thus potentially preventing an intruder from succeeding in an attack due to your antivirus software being behind on updates.
In addition, if you are subject to any regulatory compliance, IPAM can help identify information that can help you comply with the regulation. For example, if a regulation requires that a log is produced from your systems with the network IP assignments for a given time, the IPAM data can quickly be used to generate such a log on a regular basis in order to get into and remain in compliance with the regulation.
IP address conflicts (aka duplicate IP addresses in use on the network) are one of the most devastating issues that can happen on an enterprise network.
Source: David Davis
While security and compliance are both very important, IPAM is also quite helpful in order to provide you with general information on the state of your network and all of the IP addresses being used at any given time. For example, information can be collected on whether an IP is static, dynamic, reserved, or in another status. In addition, data such as MAC addresses, DHCP leases, hostnames, and more can be collected and viewed in order to help you get a solid overview or detailed report on what is happening on your network.
If your company does not have an IPAM strategy in place, it may be time to look at getting one in place. With all of the new devices and services in need of IP addresses today, keeping track of all of them on your network without an organized plan could become quite a mess. Depending on how large your company is, you might be able to do something simple in-house, or may need to make an investment in a solution that can provide you with the features and customization you need for your company.
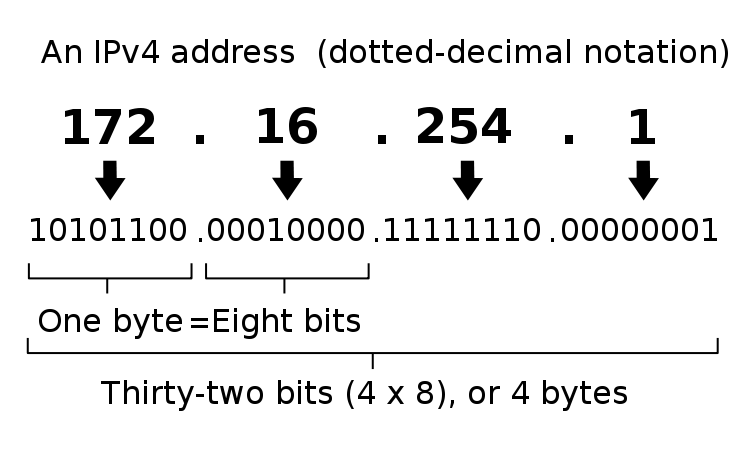

How IPV4 and IPV6 addresses are formed. Source: Wikipedia
If your company and/or network is small enough, it may be possible to use an in-house solution such as tracking IP address usage in one or more spreadsheets. Of course, if this method is not diligently maintained by all parties involved, the one or more pieces of information can become outdated, and thus next to useless to someone trying to get a report or analyze a potential security or compliance issue. Of course, a more robust in-house solution would be a bit better, such as developing your own reporting system.
As technology (and employees) change over time; however, in-house solutions can become increasingly difficult to use and/or maintain. Thus, while the financial investment of an in-house solution may not be large, it can be beneficial at some point to move to a system that you can use without the added worry of maintenance.
A solution maintained by an outside source can help you keep an up-to-date and easy to use system that you can use for the long-term. This, of course, assumes that you have the funding to do so and are able to take the time to carefully choose a vendor that will also be around for the long term. As you can see, each approach has its own strengths, depending on the size and financial state of your company.
If you are looking to begin using IPAM, as well as other cloud services, why not try out Morpheus, which makes provisioning, scaling, and maintenance of your apps and servers a breeze. In addition to having an excellent IPAM solution, Morpheus allows you to provision databases and servers quickly, and have your app up and running in no time! If you are looking to speed up website or app performance with load balancing, then Morpheus offers an incredible service for this, allowing you to provision additional servers quickly so that scaling up is quick and easy.
Using the available tools, you can also monitor the various parts of your system to keep track of uptime, response time, and to be alerted if an issue does arise. Morpheus has an excellent alerting system that helps to minimize false alarms in order to help you stay more productive in your day to day activities.
In addition, Morpheus has a clear, concise, easy-to-use interface that makes accomplishing your tasks a breeze.

The Morpheus interface is clean and easy to use. Source: Morpheus.
With Morpheus, you can provision apps in a single click, and the service provides ease of use for developers with APIs and a CLI. In addition, backups are also automatic, and you can have redundancy as needed to avoid potentially long waits for disaster recovery to take place. So, with all of these advantages, why not register an account today and take advantage of all that the cloud has to offer?