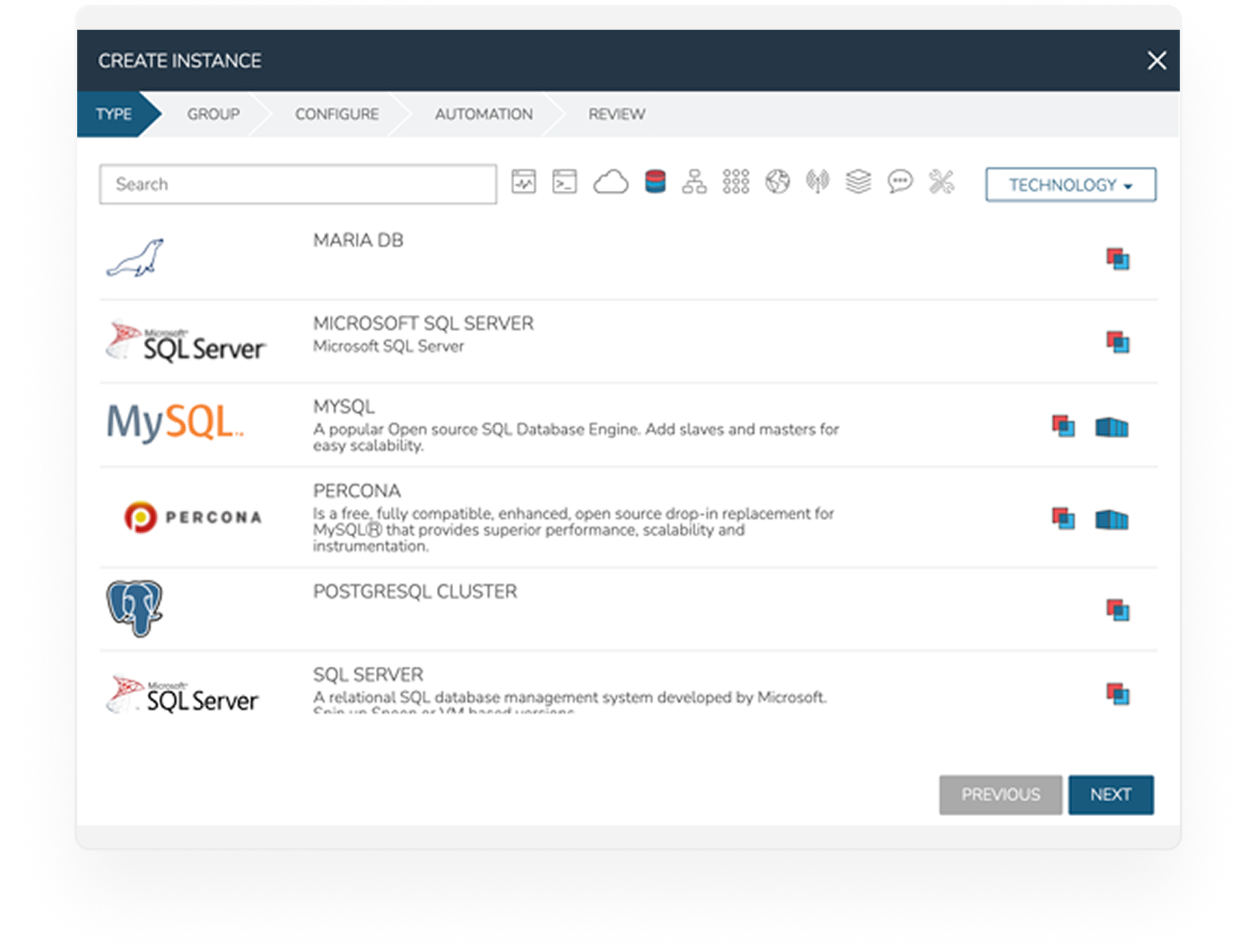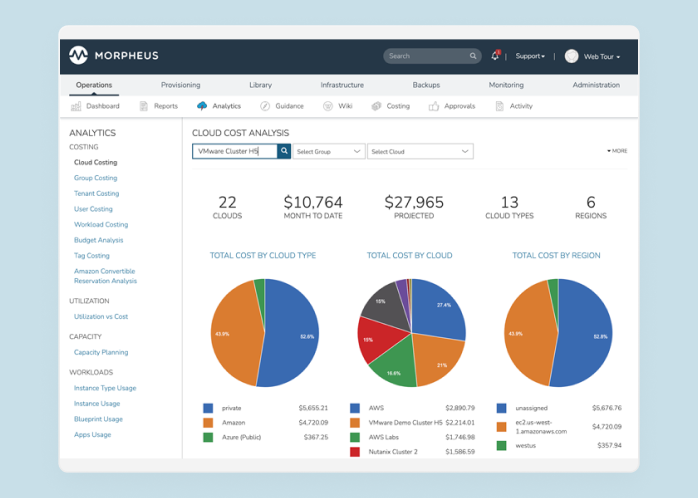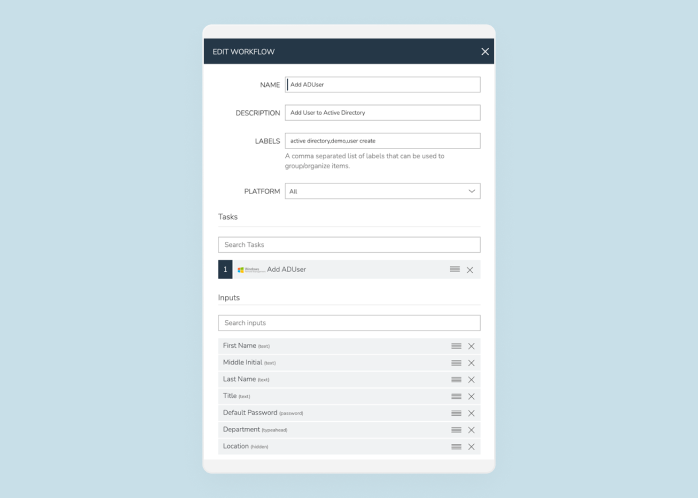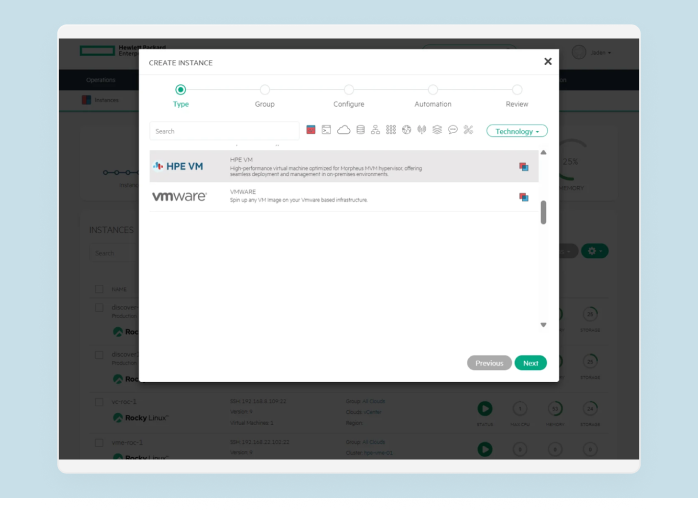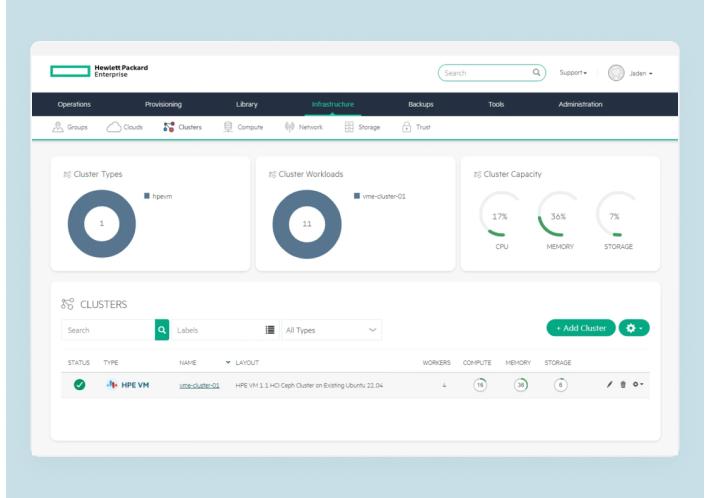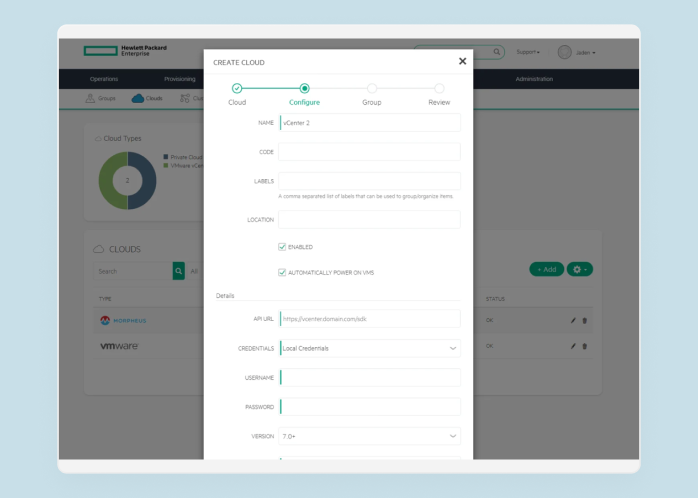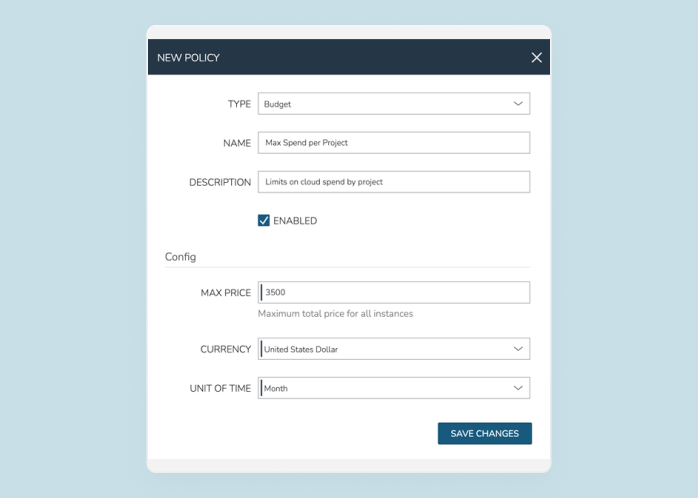
Organizations often face the challenge of shadow IT – the use of technology without the approval and governance from IT Ops, Security, or Finance teams.
Take a look at multi-tenancy, identity provider mapping, access controls, policy enforcement, and more.